Five months ago I began running my first internet-facing server in ten or fifteen years. I’ve been running a number of blogs during that time, and put up a number of websites, but all hosted on someone else’s machine, so I didn’t have to worry much about security. Switching to a VPS1 put me front and center having to worry about security…and how the internet has become a lot rougher place, behind the scenes, over the years.
Recently I noticed that my /var/log/btmp file — whose purpose I never really knew before — was getting quite large. Turns out that file records every failed login attempt. In my case that was exclusively for ssh access2 since I don’t expose any other kind of service involving user login.
This led me to doing some things to harden my server3. But it also gave me an opportunity to study just how many login attempts — attacks — there were during those months.
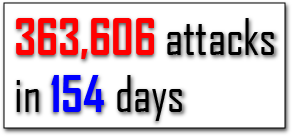
The answer was amazing: there were 363,606 attempts to gain access to the server during a 154 day period. That works out to be an average of 2,361 attempts every 24 hours, or nearly two every minute of every day.
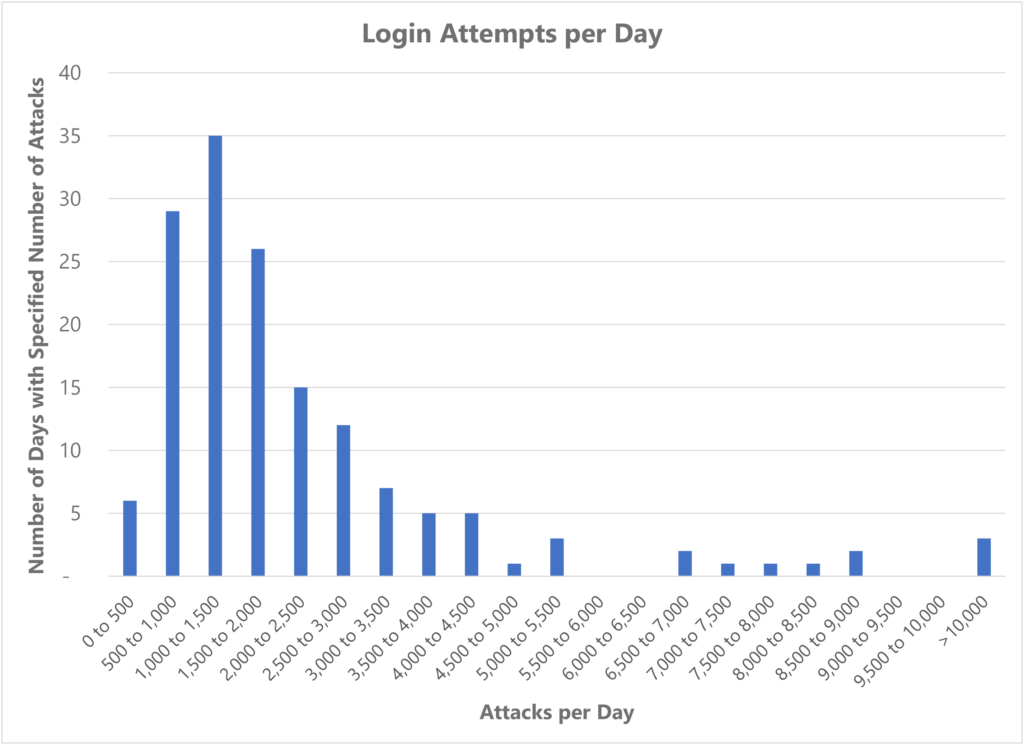
The rate varied by day, though. Christmas Day 2021 saw 20,104 attacks, nearly one every 4 seconds. New Years Eve was almost as bad, at 15,813 attempts.
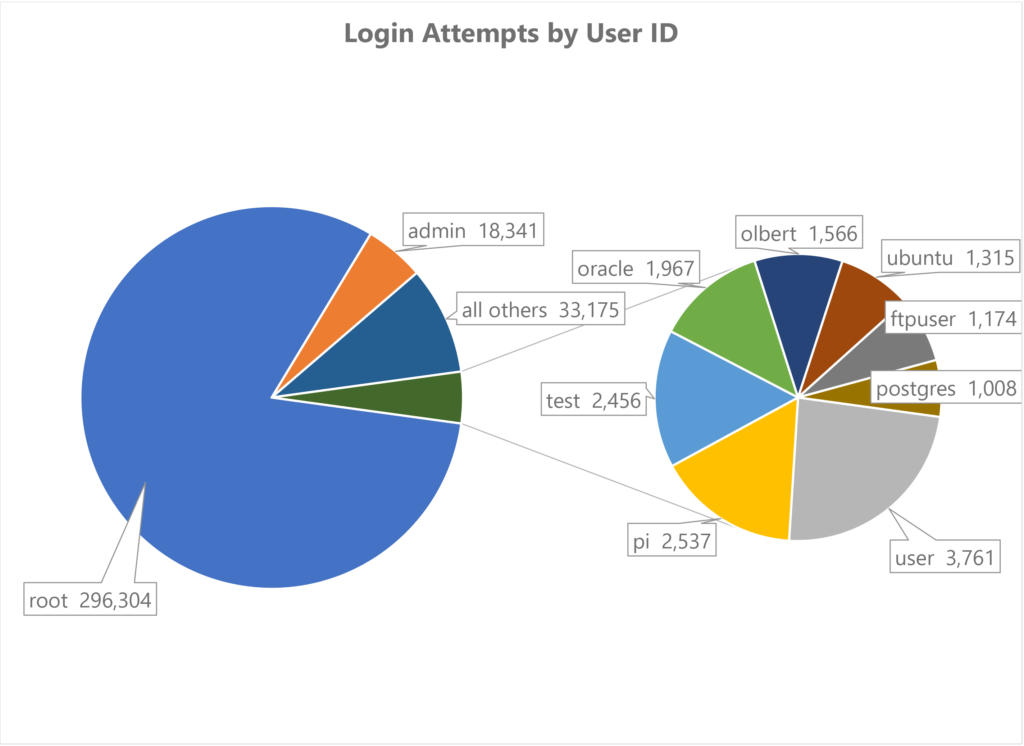
When a login attempt is made the attacker has to guess both a user name and a password. The logging system keeps track of the user names, which weren’t random:
root is an obvious choice, since that’s the default superuser account on any Linux system…which is why it’s also one of the user IDs that’s automatically rejected, on most systems, when logging in remotely. Attackers probably use it because, if left open, it’s the most powerful account available, and it didn’t used to be so heavily guarded.
pi is interesting because that’s the default user account on a Raspberry Pi, inexpensive and ubiquitous computers that are often run by people just getting their feet wet and so probably don’t know how to lock down their hardware against threats. Some of the other names are similar defaults for specific software packages (e.g., databases).
But kudos to those attackers who speculated my ego might have led me to using my last name as a user ID :). Interestingly, mark was tried…but only 13 times out of all those attempts. In fact, it was tried less frequently than 12345. Go figure.
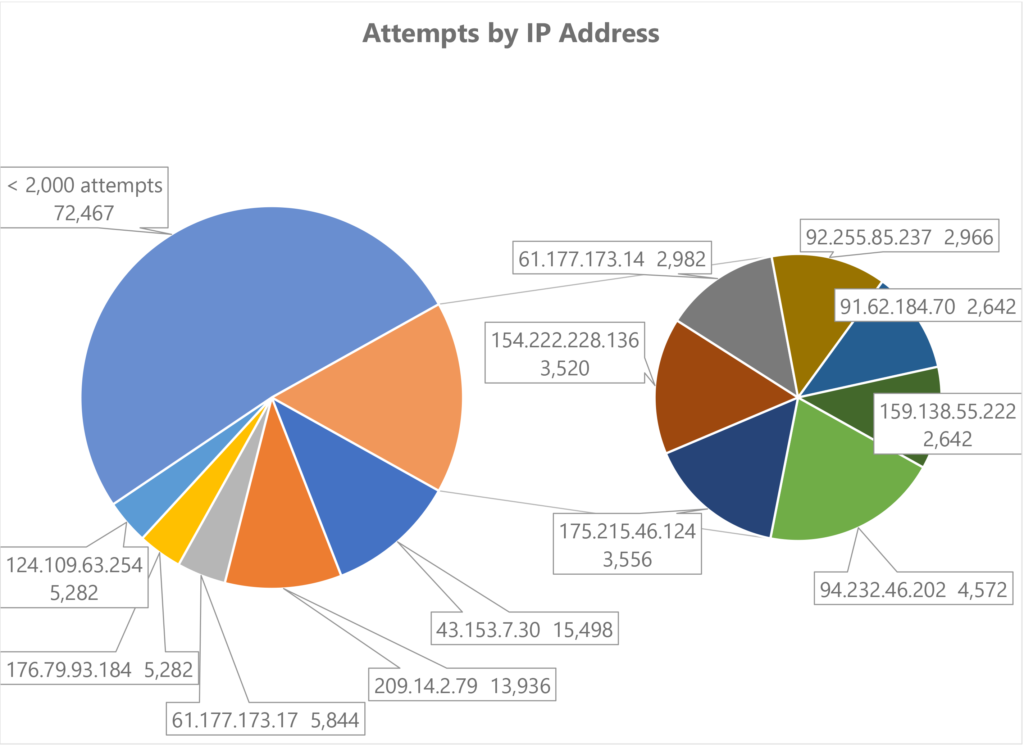
The attacks came from around the world, from almost 1,700 IP addresses. Which means some IP addresses were more active than others. Here’s the detail on the top attackers:
Looking up where those IP top addresses appear to be physically located shows they’re mostly from China, Korea, Russia, etc., places that aren’t too surprising.
But what is surprising is that the most frequent source of attacks — 15,498 in that 154 day period — came from Washington, D.C. From an address which has no catalogued human-readable name4.
I wonder if I’ve managed to offend someone in the Federal government… :).
on Hostwinds; check them out if you’re in the market for a VPS, I’ve been very impressed with both their price performance and their tech support ↩
for the non-technical visitor that’s the way you interact with a remote computer as if you had a terminal hard-wired into it ↩
specifying a non-standard port for ssh access, and setting the firewall to block IP addresses after a small number of failed login attempts ↩
most IP addresses link to names, like www.theboilingfrog.net, but they don’t have to, and often don’t if someone is trying to hide their identity ↩

2 thoughts on “A Wee Bit More Dangerous…”
Very interesting. It’s also be interested to see a follow-up article analyzing any suspicious traffic going to the login/administrative pages for your blogs.
“I’d”, not “it’s”. Thanks autocorrect.